What is %LOCAL APPDATA%\CEF?
Some people found %LOCAL APPDATA%\CEF on their PCs. AdwCleaner detects this folder as malicious.
But usually %LOCAL APPDATA%\CEF is a folder for storing data created by applications using CEF.
The Chromium Embedded Framework (CEF) is a simple framework for embedding Chromium-based browsers in other applications:
https://bitbucket.org/chromiumembedded/cef
How dangerous is CEF?
Usually CEF folder contains USER DATA subfolder. It also contains subfolder related to the CEF applications.
My verdict: %LOCAL APPDATA%\CEF cannot be marked as malicious, because it is only a container for sub-folders. You do not delete Program Files if one sub-folder is bad.
How to remove CEF malware?
Some CEF applications may contain adware/spyware etc. In this case I suggest you to delete a subfolder related to the malicious application.
Some legitimate application like Steam, Google Widevine use CEF.
Be careful to avoid damage your PC!
You can always check your PC for adware/malware/TRojans/spyware using UnHackMe.
I use UnHackMe for cleaning ads and viruses from my friend's computers, because it is extremely fast and effective.
1. Download UnHackMe
for free UnHackMe removes Adware/Spyware/Unwanted Programs/Browser Hijackers/Search Redirectors from your PC easily.
UnHackMe is compatible with most antivirus software.
UnHackMe is 100% CLEAN, which means it does not contain any form of malware, including adware, spyware, viruses, trojans and backdoors. VirusTotal (0/56).
System Requirements: Windows 2000-Windows 8.1/10 32 or 64-bit. UnHackMe uses minimum of computer resources.
2. Double click on UnHackMe_setup.exe
You will see a confirmation screen with verified publisher: Greatis Software.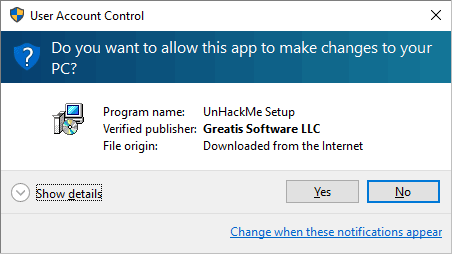
Once UnHackMe has installed has installed the first Scan will start automatically
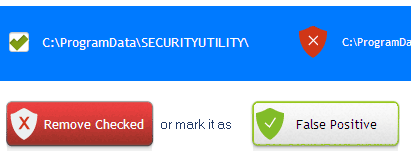
3. Carefully review the detected threats!
Click Remove button or False Positive.Enjoy!